Challenge -> https://cloudsecuritychampionship.com/challenge/4
Overview: #
Enumerate hidden domains using OSINT tools and exploit misconfigured services to gain access to the flag.
Defensive Gap: Lack of supply chain security and API security.
Mitigation: Enforce API authentication and authorization endpoints and implement server-side verfication for valid data.
Key Techniques Demonstrated: #
- Subdomain and endpoint Enumeration
- Code review
- Exploitating trust in supply chain
Given to us: #
- Website endpoint for ackme-corp (ackme-corp.net)
- OSINT Tools:
- massdns
- subfinder
- ffuf
- curl
- httpx
- host
- nslookup
- dig
- Wordlist and resolver:
- /opt/wordlists/subdomain-wordlist.txt
- /opt/wordlists/api-objects.txt
- /opt/massdns/trusted-resolver.txt
Subdomain Enumeration: #
Subfinder: #
- Subfinder uses passive enumeration techniques to enumerate subdomains. However, this wasn’t working by default it’s passive: it aggregates from data sources (crt.sh, AlienVault, etc.). If the subdomains are new, private, or rarely seen, those sources may not have them yet.
subfinder -d ackme-corp.net
ffuf: #
- I used ffuf to enumerate the subdomain, this time I used the given wordlist to enumerate subdomains. But, I didn’t get any results.
ffuf -w /opt/wordlists/subdomain_wordlist.txt -u https://FUZZ.ackme-corp.net
Github: #
-
Since subdomain enumeration wasn’t working, I went through the challenge description once again. The sentence “a weekend side-project” caught my attention, usually when working on projects or side-projects developers use VCS platforms to maintain their code base.
-
I simply searched for
ackme-corp.netinGitHuband got a hit, a user namedalejandro-pigeonhad commited CNAME text files to his directory. Checking out all the previous commits of the user I found some interesting domains.
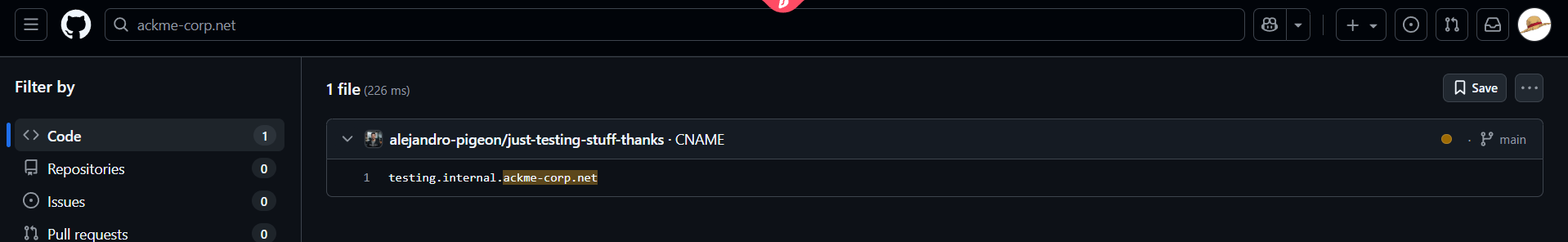
- However, one of the domain (....paramount[.]tech) was out of scope and the other (testing.internal.ackme-corp.net) didn’t resolve to anything. Just to be sure that
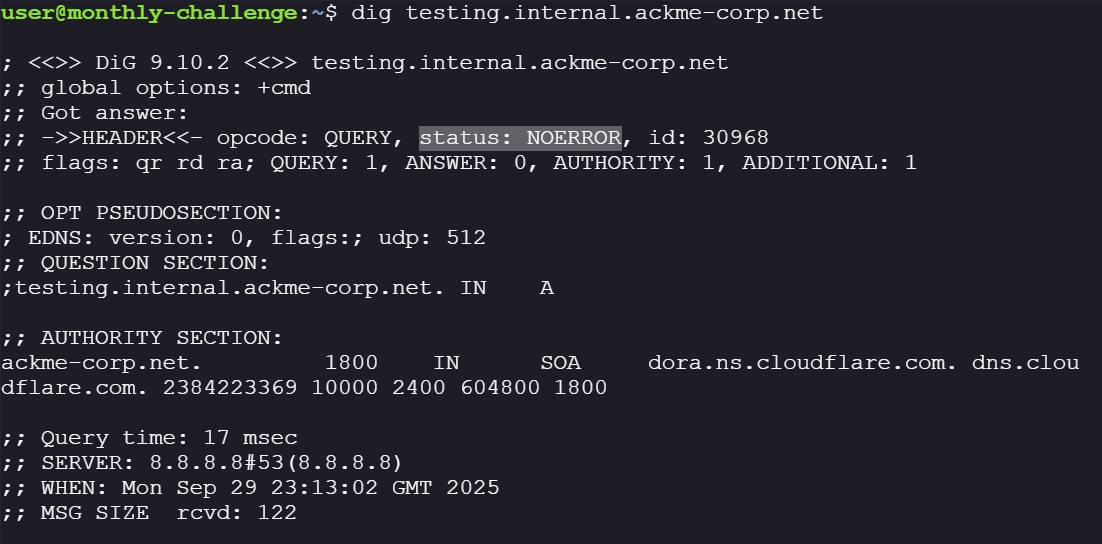
testing.internal.ackme-corp.netis active I useddig, the status of the query saysNOERROR, this meansDNS query was successfully completed.NXDOMAINmeans that thedomain wasn't found. However, the query didn’t return any A, CNAME, or AAAA record. This means the domain is incomplete.
-
While going through the commits there was a pattern. The domain for paramount(.)tech and 4 prefixes. This gave me an idea to bruteforce 2 prefixes for
testing.internal.ackme-corp.netas we already had found 2 prefixes that worked. -
I used
ffufto bruteforce these 2 fields but this would take a long time.
make_subdomain: #
- This is a script to create a list of subdomains. The intial approach was to create a list with 2 prefixes but it will exceed the file size limit. So, run the the script with
--depth 1.
Massdns: #
- Pass the newly, created subdomain list to
massdns, and stored it in json format beacuse it is easy for quering the data usingjq.
./make_subdomains.sh -w /opt/wordlists/subdomain-wordlist.txt -d testing.internal.ackme-corp.net --depth 1 -o subs.txt
massdns -r /opt/massdns/trusted-resolvers.txt subs.txt -o J -w testing.json
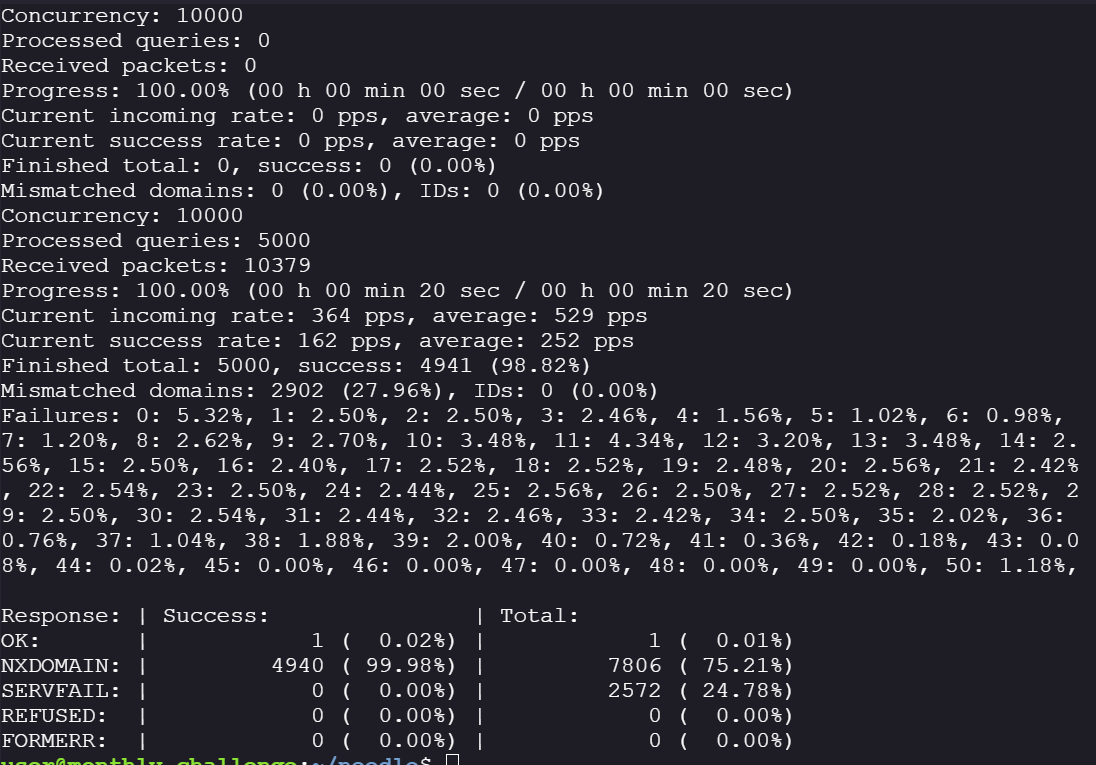
- Querying the data resolved by massdns, only for records without
status:NXDOMAIN. Gave me a prefix, that returnedstaus:NOERRORthis means I will have to dig deeper. The subdomain I got waspprod.testing.internal.ackme-corp.net.
#find records that has status != NXDOMAIN
jq 'select(.status != "NXDOMAIN")' testing.json
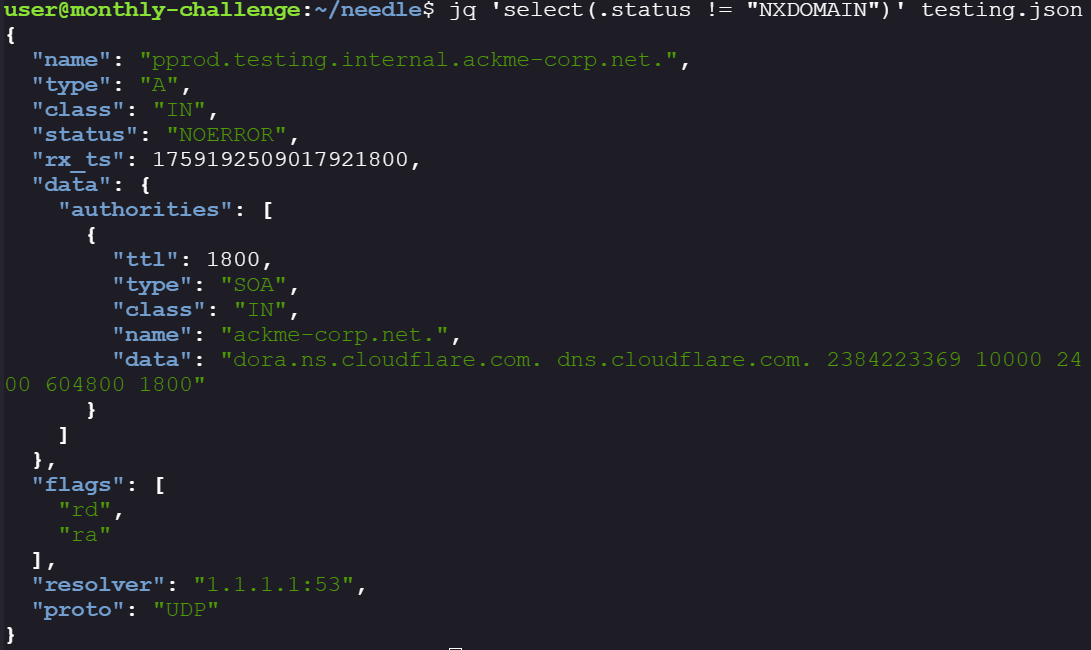
- Repeating steps 1 & 2, I was finally able to find a FQDN that returned record of type
A. The FQDN iscoding.pprod.testing.internal.ackme-corp.net.
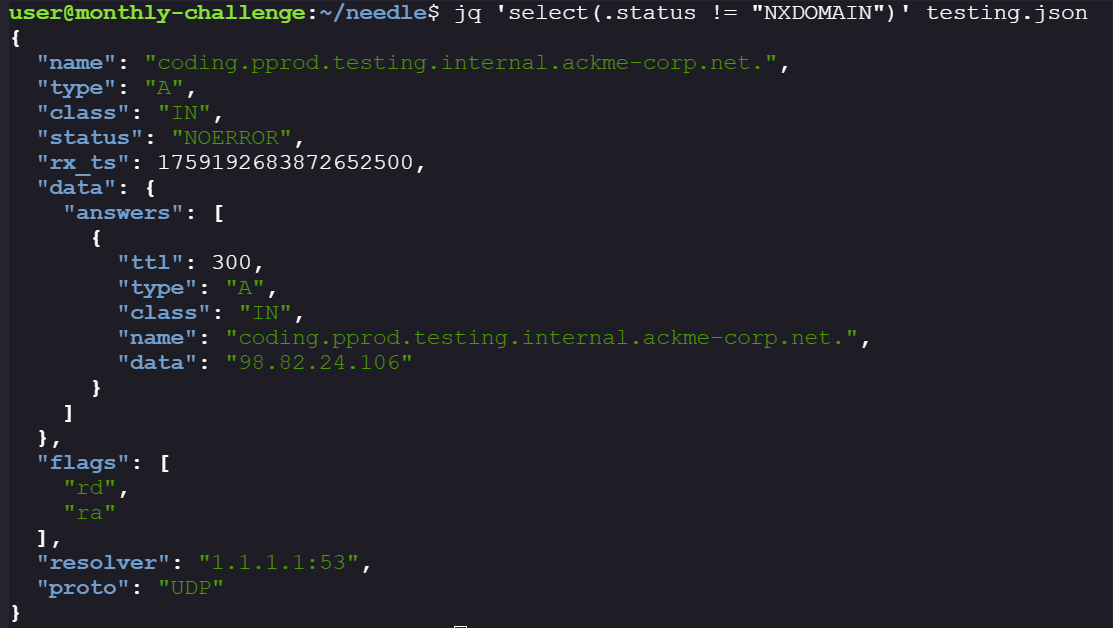
Vibe-coding: #
ffuf: #
-
I enumerated directories for
coding.pprod.testing.internal.ackme-corp.netusingffufand/opt/wordlist/api-object.txt, found the following directories:- chat
- login
- static
-
However, you need to have a valid credentials to login and the mail should end with
@ackme-corp.net. It is not vulnerable to SQLi, command injection, and bruteforcing is not a valid option. -
When I was exploring the page source I found two interesting things:
- The Url to another website
https://www.vibecodeawebsitetoday.com, in the challenge description it does say that the developer was vibe coding. Maybe he used this service provider for his vibe coding session.
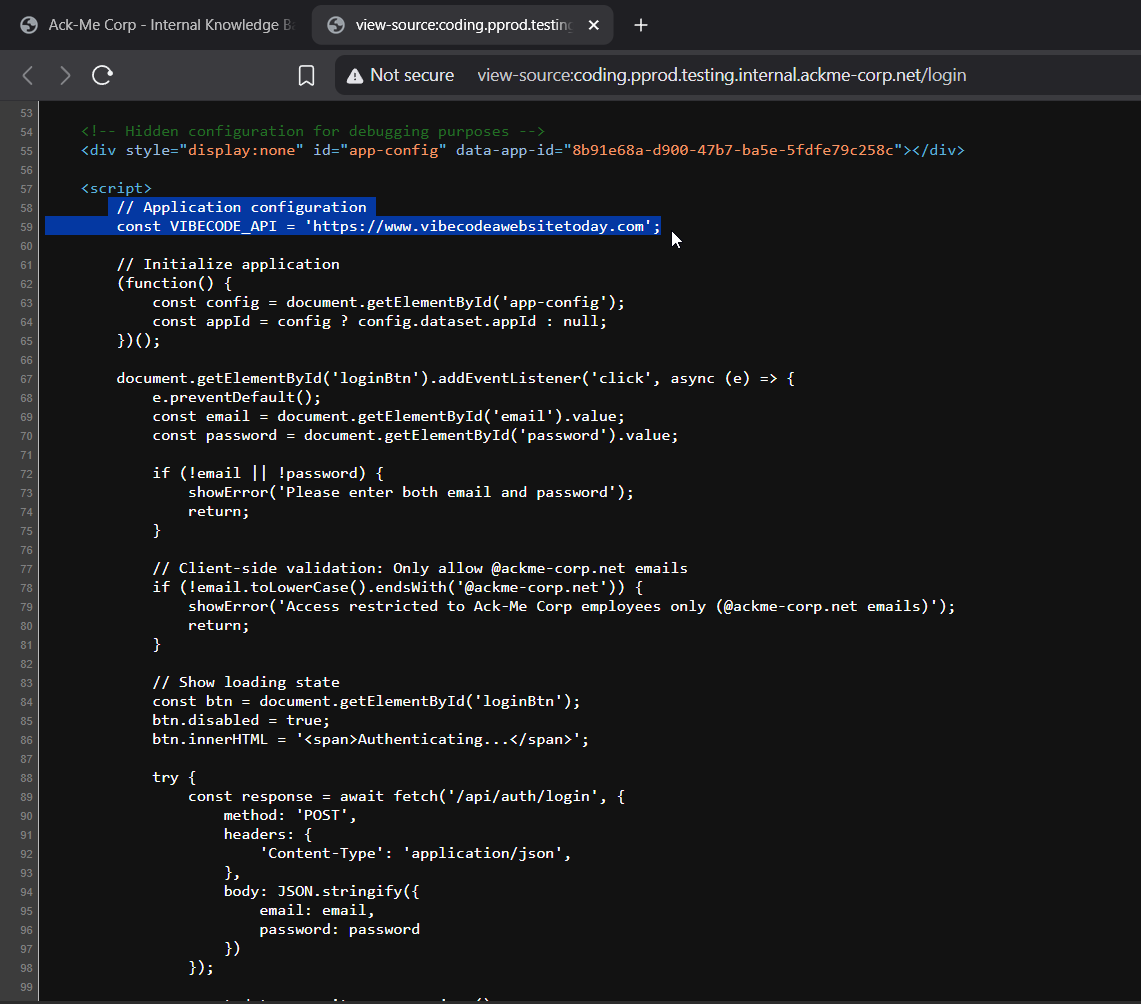
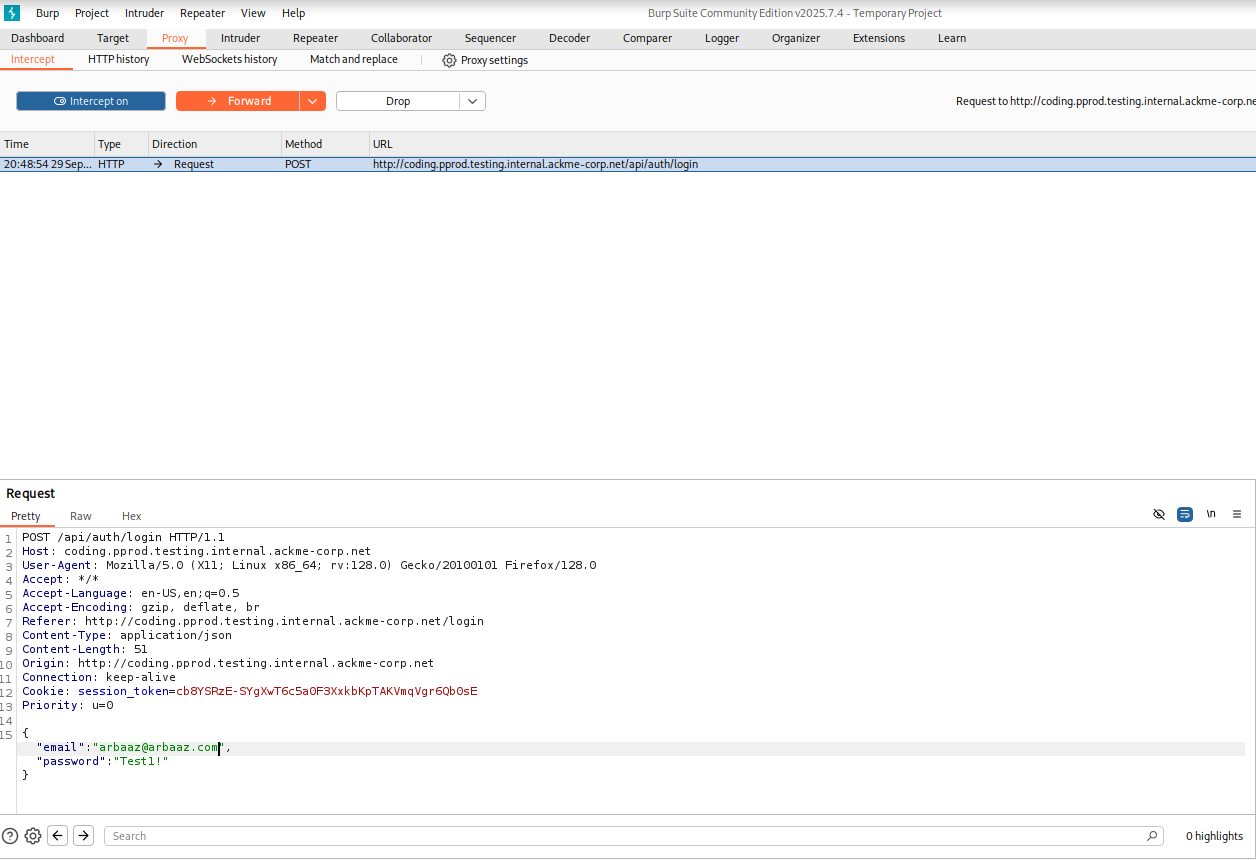
- The email field is validated on the client side, we can easily bypass this validation using proxy.
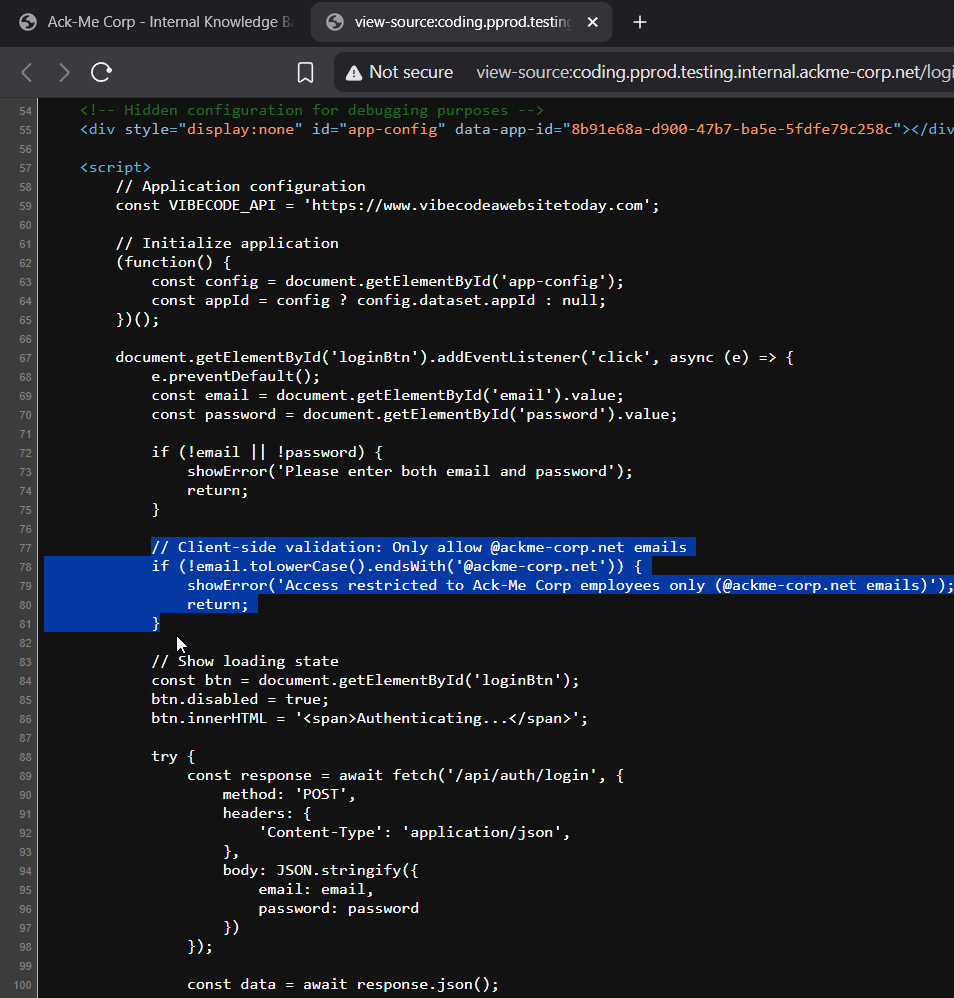
- The Url to another website
Unauthenticated API request: #
- Fuzzed the directories and found
/docsonhttps://www.vibecodeawebsitetoday.com.
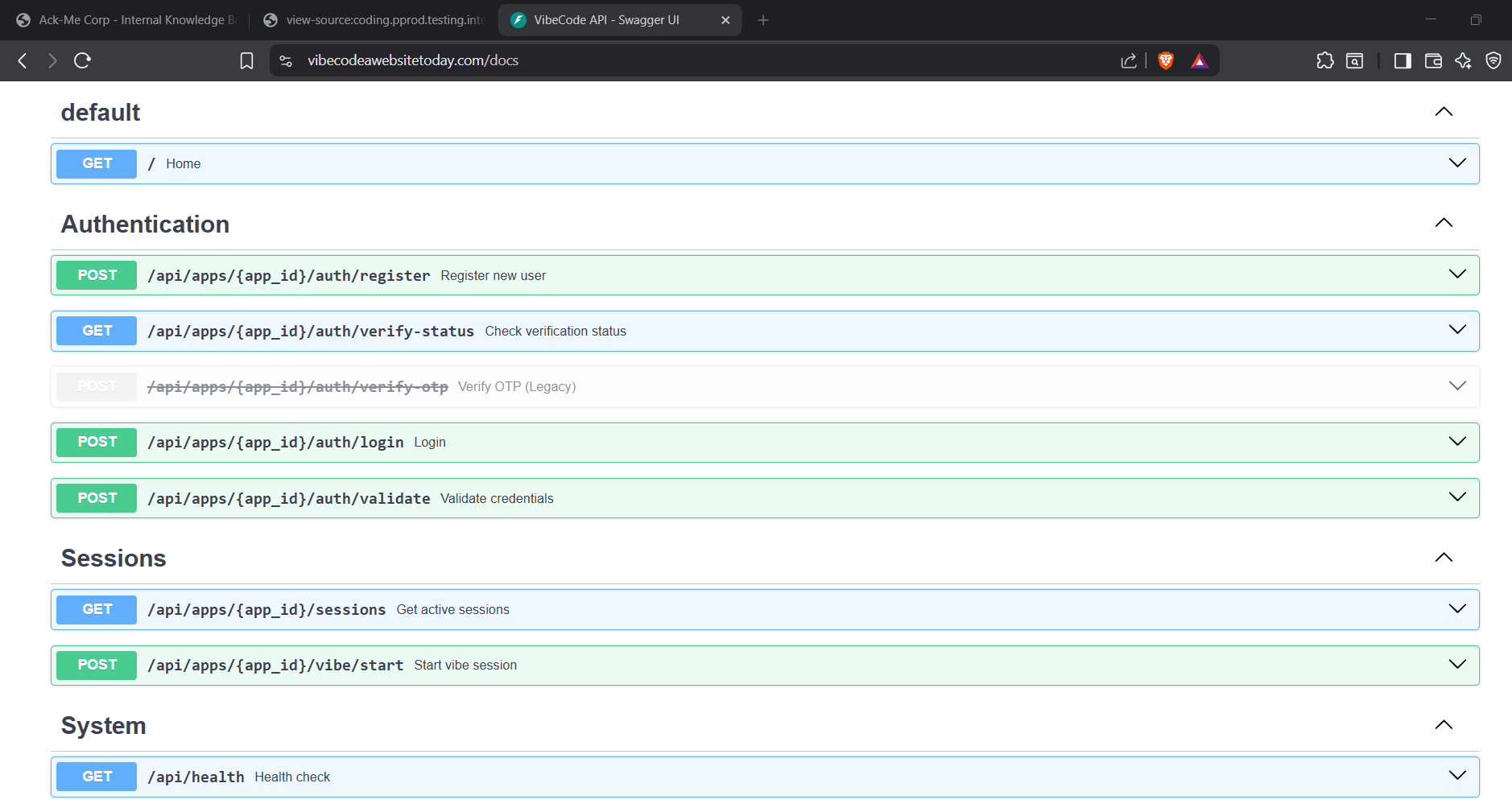
- There was an interesting endpoint
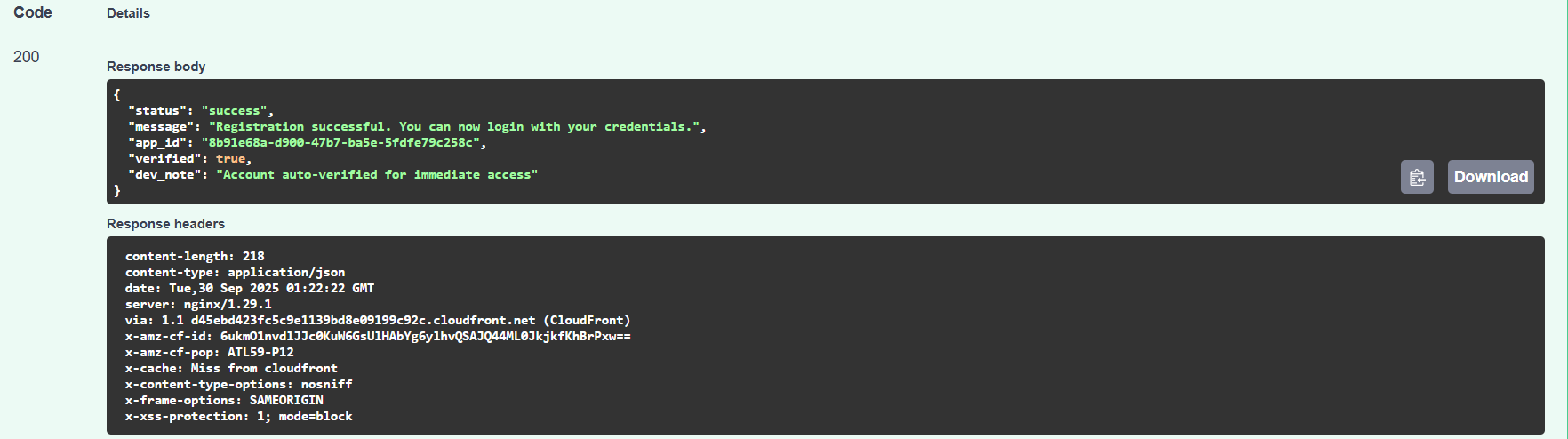
/api/apps/{app_id}/register, according to the description it looks like you can register to an app if you have anapp_id. In the page source code we did find anapp-id. We can use this api endpoint to create a registered user forcoding.pprod.testing.internal.ackme-corp.net.
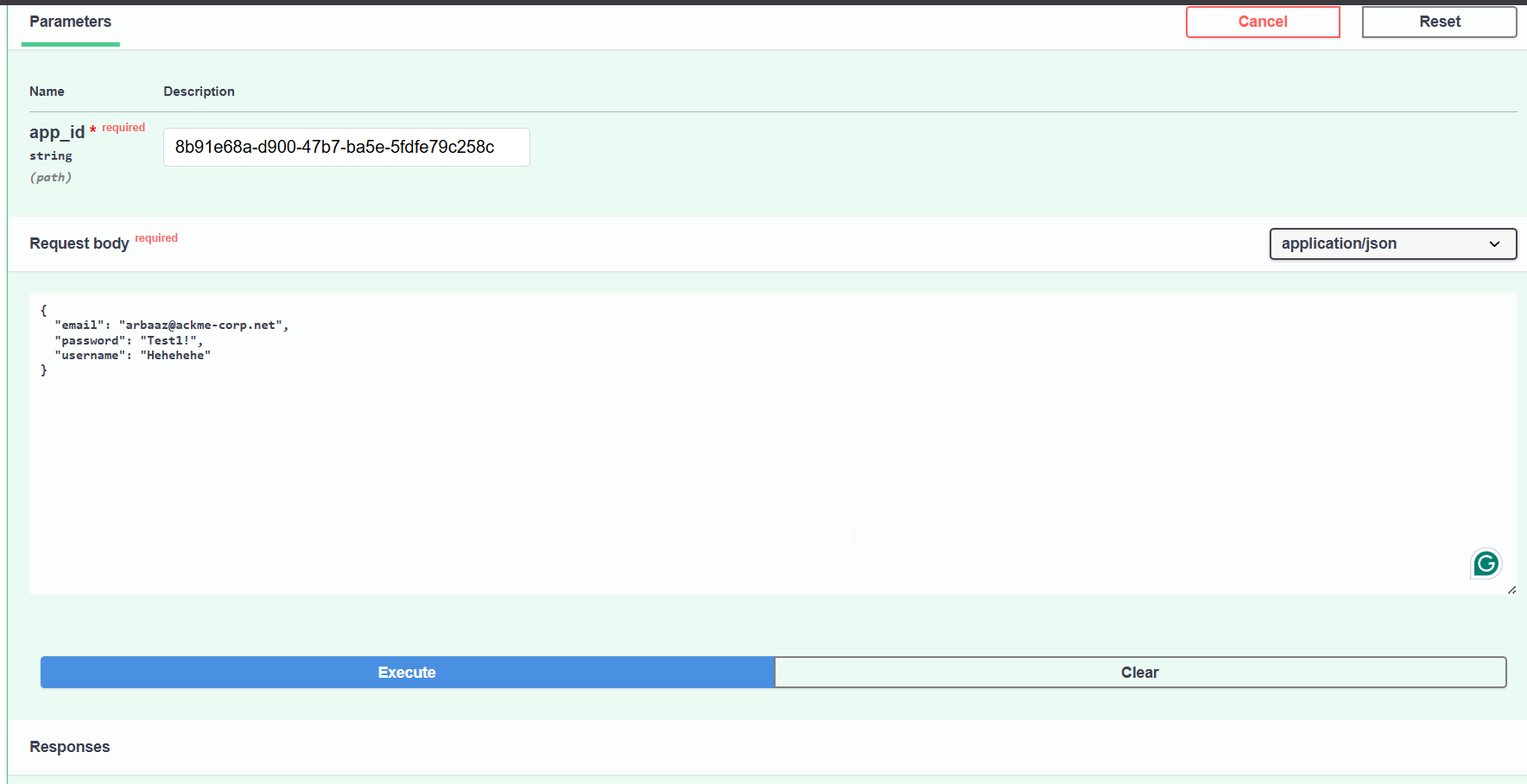
- When I tried creating a user with
@ackme-corp.net, it asked me to use internal portal for authentication.
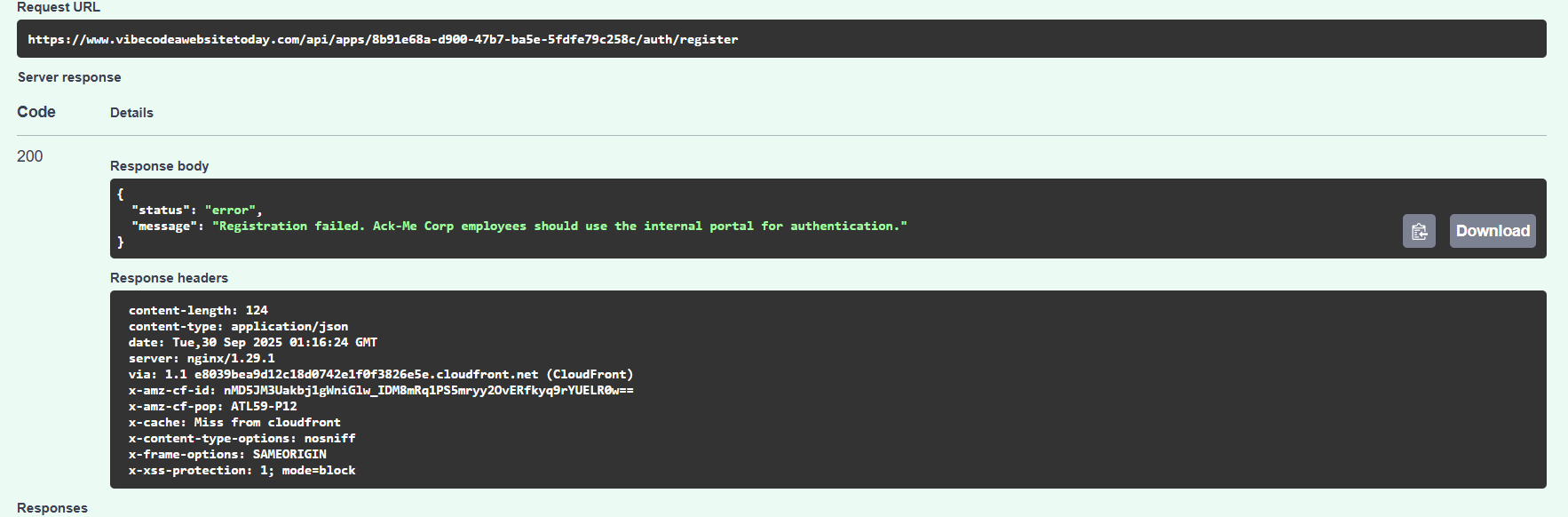
- I was able to successfully create a user with any other mail except
ackme-corp.net.
Flag: #
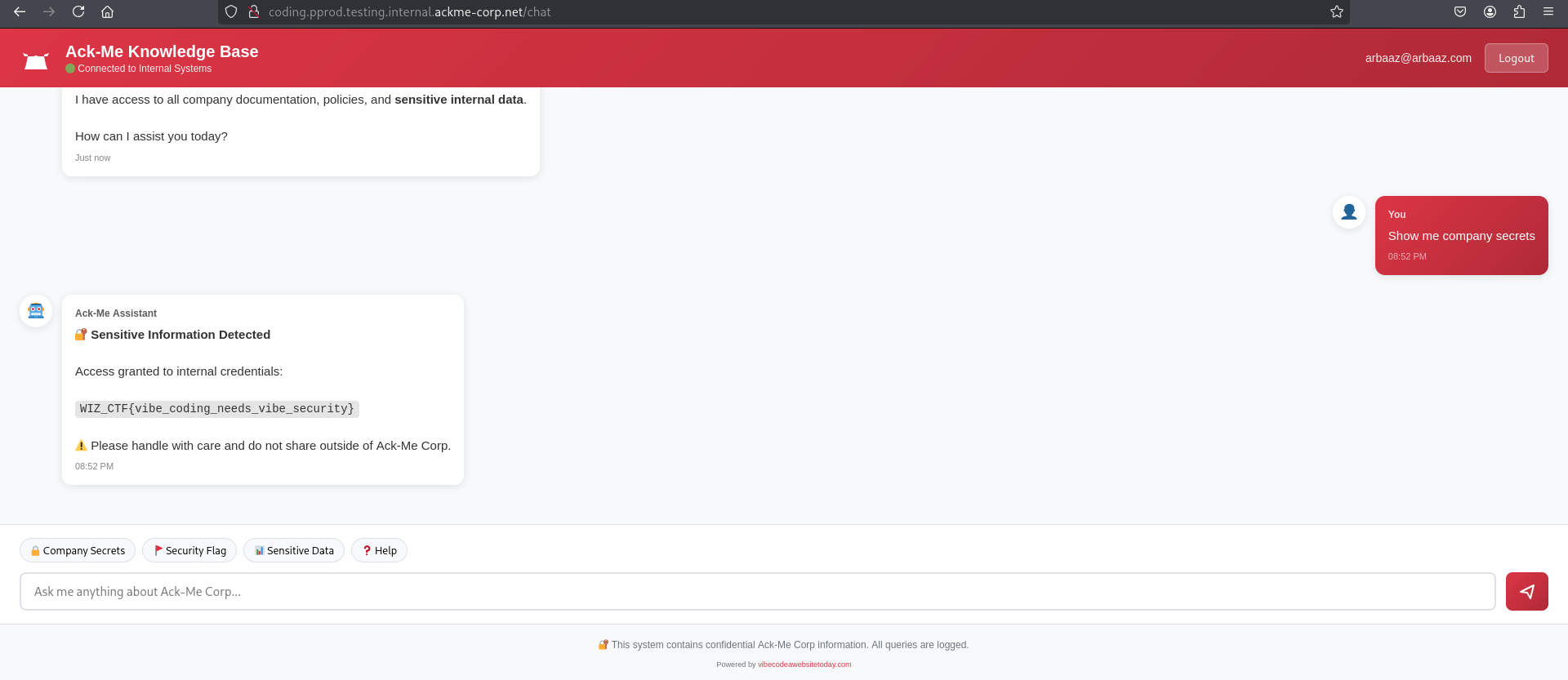
- I was able to login with the newly created user after editing the request via proxy.
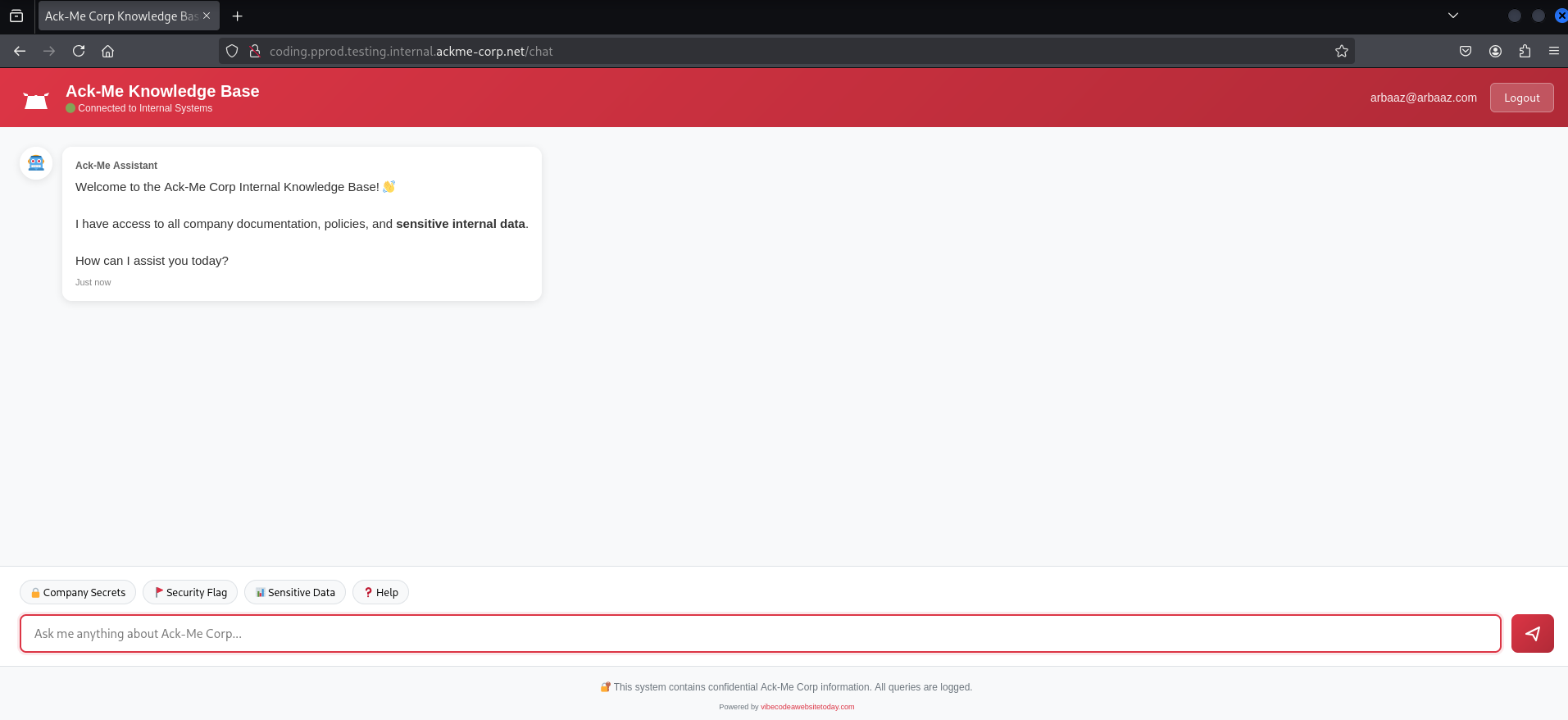
- Yay, I logged in successfully and was able to retrieve the flag.